Anonymity with Ethereum is hard. It’s a public blockchain, after all.
Sure, you can create your seed phrase offline or with a hardware wallet, but as soon as it comes to moving funds to your fresh accounts you should expect that eyes will see that transaction – even years later.
Even with all the proper steps taken to create a cold wallet, the currencies you put into those accounts still come from somewhere. And somewhere wasn’t in your control.
Typical Transactions
Let’s take the classic example of where that money comes from: an exchange.
When you sign up for an exchange like Coinbase, you go through KYC. They know who you are, how much you buy, and where you send it.
So, when you send funds from the exchange to your secure cold wallet, they have access to this transaction. They could deduce that wallet as yours (and share that info with the IRS or NSA, etc). Even if you use a mixer, the exchange will still see this and flag or even block your address.
It’s all connected, forever.
Now, in this pure example, nobody else could deduce that this cold wallet is yours. Randos on Twitter wouldn’t be the wiser. On-chain it’s just another transaction.
This is basic pseudo-anonymity: the public doesn’t know that this account is yours, but there is some trail that could identify you to someone. In essence: you are not guaranteed anonymity.
The risk of exposing your addresses and losing that pseudo-anonymity is exacerbated by participation in the network:
- Transferring funds
- Registering ENS
- Buying NFTs
- Using DeFi
- Transacting with platforms like God’s Unchained
So it’s good to arm yourself with some principles & rules for using Ethereum so you can guard yourself from exposure.
Principle #1: Be Public AND Private
Use specific public & private addresses and keep them completely separate.
With this one principle, you’ll be able to maintain pseudo-anonymity with one reason: intention.
When you commit to using a public address, you acknowledge and understand the public nature of the chain itself. This inherently will train you to think between public and private transactions.
Always think: “Should I use my public address for this transaction?”
For example, I use my public address for:
- Registering ENS & mapping it to my Twitter
- Connecting to God’s Unchained
- Building example transactions for education
- Kicking the tires on DeFi platforms before diving in
- Linking with 3box and Satellite
Not everything can be private; rather than deprive yourself of using various protocols, use a public address with them instead.
With that, you can expand into a few simple rules (and a handy flowchart).
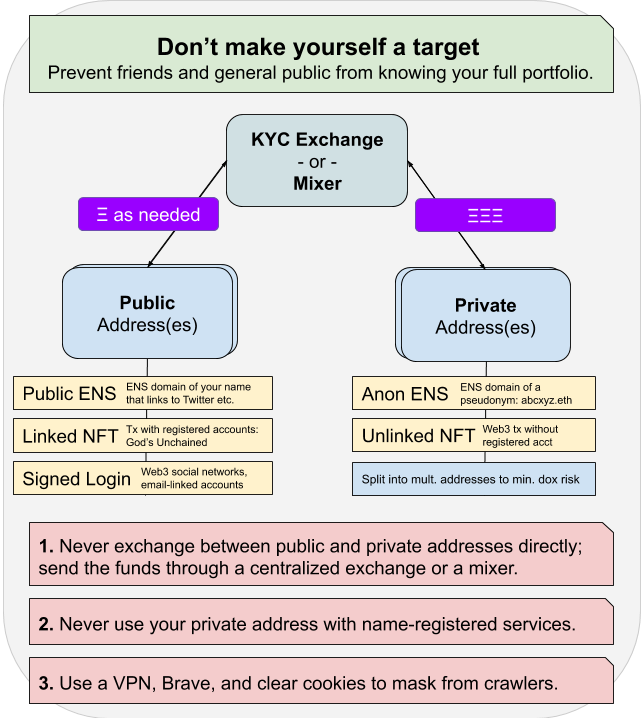
Rule #1: Use multiple addresses
Not only should you split between public and private addresses, but you should use multiple of each to diversify your pseudo-anonymity.
Maybe you don’t want two public protocols to know that you’re using the other. Consider using a public address for each.
If you want to guard your private address against the risk of exposure, split it into multiple. Use one for DeFi and one for hodling – this way no one can determine your full net worth by uncovering one account.
Use one for a public pseudonymous Twitter account.
With multiple addresses, you limit your exposure to connecting them all.
Unfortunately, as you expand your address collection, your fees for moving those funds around grows. Be sure to consider transaction fees into your privacy plan.
Rule #2: Never cross streams
Never transact directly between your public and private addresses.
Only send assets to your addresses from a centralized exchange (or a mixer).
Due to the way centralized exchanges are set up, they essentially act as a mixer with the way their receive/send currency. So, if you need to send money from your private address to your public one, send it to your exchange first and disperse it to your public address in two transactions to ensure you leverage the mix properly.
Obviously this does still leave you exposed to exchange deduction, but it will keep the public out of the know. You’re not trying to hide from big brother, are you?
Rule #3: Use Brave, a VPN, and Tor
Looking to supercharge your privacy?
Use Brave browser and always clear cookies & local storage when switching between public and private accounts. This prevents individual applications from tracking that two addresses could be linked to the same user.
Use a VPN or Tor to totally obfuscate your internet browsing history from your ISPs.
When you actively commit to dividing transactions between multiple public and private addresses, you’ll be well on your way to concealing your true net worth & activity; limiting your exposure to being a target for crypto theft and questions from your mother-in-law.
What tips do you have?
